Between 500K and 500M sets of credentials have been compromised over the recent years, according to various sources. Just last week, a compromise of an educational service Edmondo has been reported to expose as many as 78M user accounts.
At the same time, individual users are exposed to so many passwords that it is not humanly possible to remember unique passwords for every one of dozens or even of hundreds of web services we use every day. More than 60% of internet users reuse passwords 5 or more times and with a good reason. An average American adults is forced to create over 50 passwords just to get through their day to day tasks.
A typical botnet credential attack can include as many as 25K-100K agents or bots.
As a result password reuse is flourishing and hackers are there to take advantage of it. The recently published *Verizon 2017 Data Breach Investigation Report” shows that 40% of all security incidents (based on the actual security issues statistics collected) occurred because of the credentials problem. And those stats do not even include bots!
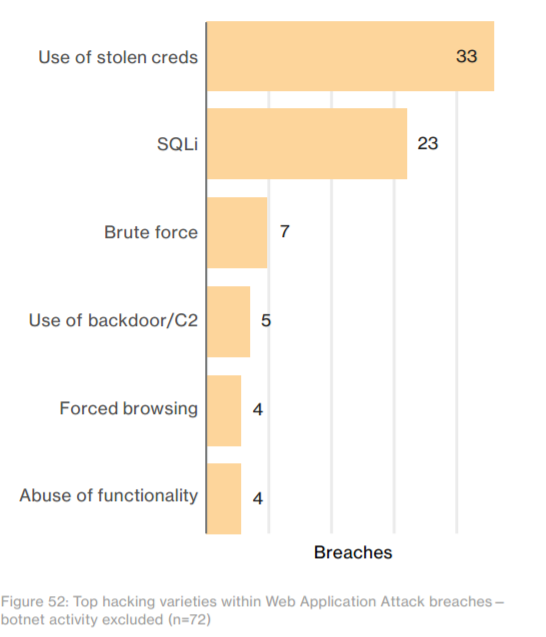
The problem is common across all industries but afflicts the most damage in E-commerce, Travel, Entertainment as we see in 2016 stats.
The danger escalates when taking into account credential stuffing and brute force (trying all the letter combinations) passwords attacks with bots. Bots are tiny automated agents that run on other people’s computers and devices without the owner knowing it is happening. A typical botnet credentials attack can include as many as 25K-100K agents or bots.
A successful attack can inflict material damage on the affected company or service.
- Compromised user accounts are used to access financial or proprietary data for perpetrator’s financial gain, for example, charging goods to somebody else’s eBay account.
- User accounts are leaked to compromise a hosted service and damage their reputation. A notable example of this is last year’s news about 500M user accounts lost by Yahoo.
- DoS of the system. When the authentication service is down, not only it brings internal IT to its knees, but also effectively shuts down any service using the corporate authentication system as an external identity provider.
- Many other industry specific incidents have been seen.
What is credential stuffing and why is it hard to beat
Credential stuffing is a type of an attack on a web service, which allows a hacker to gain access to the web service’s customer account through the “front door”. A typical case of successful attack including trying user’s credentials (user name, email and password) stolen from another site on a completely different and often unrelated web service. Credential stuffing is somewhat similar to the password brute force attack. It also provides access to the passwords. However, to brute force a password, a hacker needs significant computing power to try all the different combinations, while with the vast amounts of stolen accounts & passwords that are easily acquired on the dark web, the process in the credential stuffing attack is reversed — they are looking for valuable web services that are using the same credentials they have already gained access to. In fact, the volume of stolen credentials is so significant it has sprung to life an entire underground economy: selling databases, developing scripts/software to run credential stuffing attacks against particular websites, selling proxy-lists to make attacks more difficult to mitigate and more. Moreover, these malicious services lower the barrier to entry for malicious hackers, nor are they hard to find.
While the fundamentals of credential stuffing attacks are well known to security and operational professionals, stopping them is not an easy matter.
- In many cases (as high as 90%) attackers tend to run credential stuffing attacks against APIs for mobile clients, which is inhibiting common prevention methods such as CAPTCHA
- Botnet driven attacks are very massive ( it can take as high as 100k IPs botnet network proxies). These attacks often result in DoS, especially if company user authentication is somehow connected to additional software (e.g. CRM).
- Unlike traditional password bruteforce, Credential Stuffing attacks are fast: even a one or a two second window is enough to make dozens and hundreds of attempts. This speed of attack is no match for the typical home-grown methods of defense such as limiting request rate, fail2ban scripts and such.
Case-study. E-commerce platform
Let’s explore an example of a life credential stuffing attack stifled by Wallarm.
A Wallarm customer, a sizable e-commerce vendor was experiencing issues due to compromised user accounts. Most the issues were centered around their Customer Loyalty Program. The attackers used other customers’ loyalty points to buy products which resulted in:
- direct costs
- increased load for support team
- user dissatisfaction and thousands of one-star ratings in App Store because of user dissatisfaction
- loss in brand value and loyalty ( due to point 3)
Most of these attacks were carried out automatically (botnet) via Mobile APIs, thus making CAPTCHA and proof-of-work impossible without updating all the client applications (not an option).
Within 15 minutes of deployment, Wallarm started to detect and ban IPs suspected of bruteforcing
To achieve almost zero delays in banning, IPs to ban are exported to the edge firewall system.

Wallarm can also apply live selective blocking on the API by API basis. This approach maintains the same level of credential stuffing protection, but avoid pitfalls like entire exit IP pools of mobile operators.
Wallarm continued to track attempts, and export usernames likely to be compromised to customer anti-fraud team. Beyond immediate credential security, Wallarm’s ability to distinguish a human actor from a bot without CAPTCHA dramatically improves user sign-in experience and user retention.
For this and many other customers, Wallarm’s behavior-based analytics and machine learning enable us to detect bots and resist malicious actors when they try to adapt their algorithms to by-pass protection systems, far beyond the capabilities of the request-rating system that only help with the simplest cases.


