Polyfill.io helps web developers achieve cross-browser compatibility by automatically managing necessary polyfills. By adding a script tag to their HTML, developers can ensure that features like JavaScript functions, HTML5 elements, and various APIs work across different browsers. Originally developed by Andrew Betts, Polyfill.io injects JavaScript polyfill libraries based on the user agent or other characteristics, streamlining code maintenance. A recent supply chain attack compromised over 100,000 websites through the popular Polyfill JavaScript library. Earlier this…
On May 21, 2024, Veeam revealed a severe flaw across its Veeam Backup Enterprise Manager (VBEM) web interface that enables an unauthenticated attacker to log into the web interface as any user. Officially designated as CVE-2024-29849, the vulnerability presents a major threat with a CVSS V3 rating of 9.8 (critical). VBEM is a web-based platform that allows administrators to oversee Veeam Backup and Replication installations through a web interface console. Hence, threat actors might exploit…
Do you know what 23andMe, Jason’s Deli, North Face, and Hot Topic have in common? They’ve all been breached by successful credential stuffing attacks in the last year! An attack type that has gained prominence in recent years is credential stuffing. In this blog, we will explore what credential stuffing is, discuss current approaches to mitigate this type of attack, and their weaknesses. Additionally, we’ll share our insights on what needs to be. What is…
The Wallarm Security Research team is pleased to share the latest version of our API ThreatStats report. This report serves as a key resource for API, Application security practitioners. It emphasizes the need for a proactive stance in API security, advocating for continuous monitoring, regular updates, and the adoption of latest advanced security solutions.
API Security Threats Continue to Grow
In today’s modern Enterprises, Application Programming Interfaces (APIs) have become the cornerstone of technological integration and innovation. As the reliance on APIs intensifies, so does the complexity and frequency of security threats against them. Our 2024 Annual API ThreatStats™ Report reveals an alarming trend in API vulnerabilities with a substantial 30.15% rise in API-related Common Vulnerabilities and Exposures (CVEs), underscoring the escalating challenge facing today’s security practitioners.

Detailed Analysis of API Vulnerabilities
The report includes a detailed breakdown of the increased API vulnerabilities and categorizes these vulnerabilities into several types, including injection flaws, broken authentication, and sensitive data exposure, among others.
For example, injection flaws alone have seen a 40% increase in frequency, illustrating a growing area of concern. The technical nuances of each vulnerability type are discussed, along with real-world breach instances that exemplify their impact.
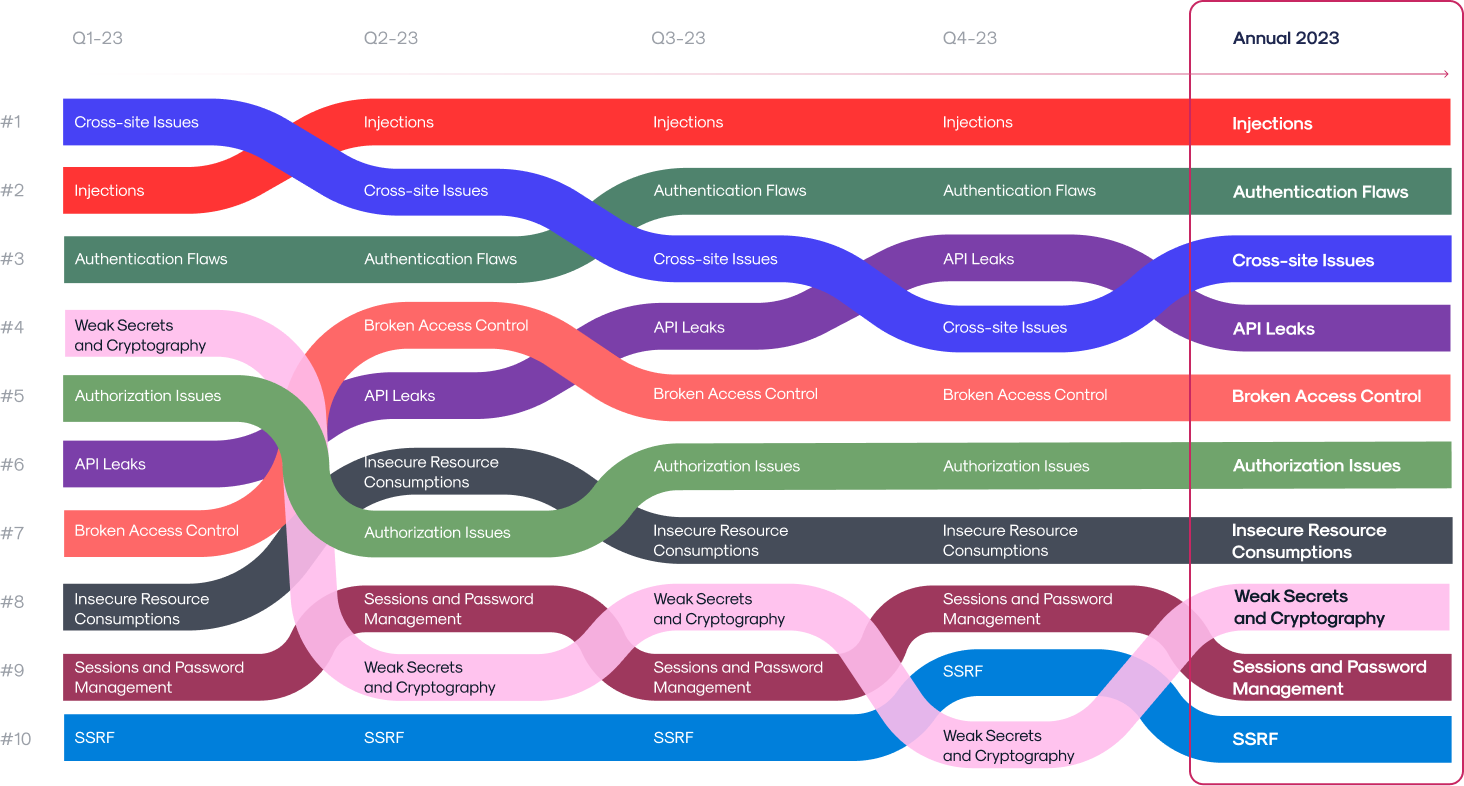
Reliance on proven frameworks such as OWASP Top 10 is a good starting point, however security practitioners need to adapt to a more dynamic Top 10 list (shown above).
In-Depth Look at API Leaks
Often overlooked, API leaks have become a critical issue, often resulting from gaps in security protocols or oversight in API management. The report details several high-profile API leaks, analyzing the root causes and subsequent data breaches. These examples highlight the need for enhanced security measures, including regular audits and robust API testing strategies. The section also discusses techniques for early detection of potential leaks, emphasizing the importance of proactive security practices.
API Security Dominated Bug Bounty Payout
In 2023, the bug bounty landscape shifted significantly, with rewards for API vulnerabilities surpassing those for traditional web flaws. The report shows increased frequency and higher payouts for API issues, notably in Broken Access Control, Vulnerable/Outdated Components, and Injection vulnerabilities. API issues garnered 1.5 times more rewards than classic web vulnerabilities, and the average payout for API vulnerabilities was 65% higher, emphasizing the growing focus on API security.
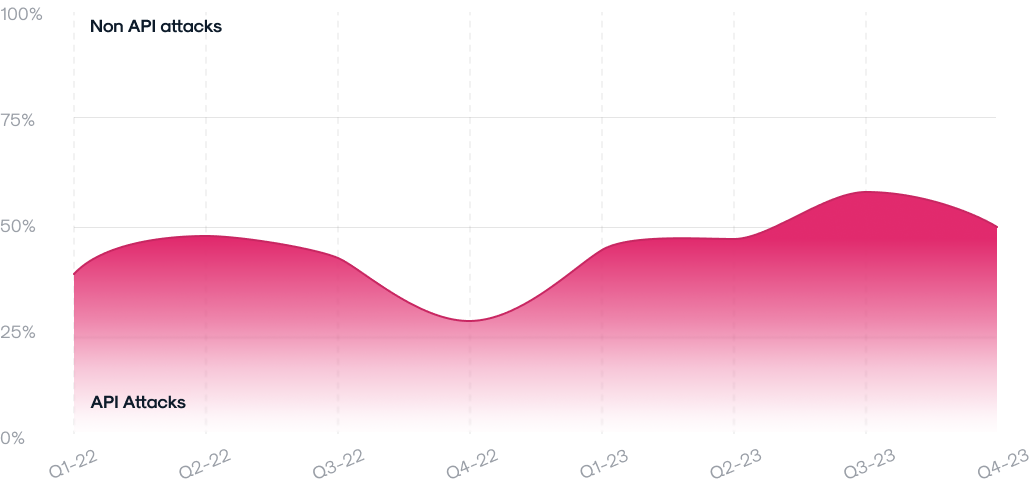
Significant API Exploits in 2023
2023 witnessed some landmark API exploits, with the report offering an in-depth analysis of incidents like the Snapchat payout and the Citrix Bleed. These case studies delve into the technical specifics of each exploit, discussing how they were executed and the broader implications for API security. The analysis also explores potential preventative measures and response strategies, providing valuable lessons for security professionals.
Based on Data Analysis
The 2024 API ThreatStats™ Report encapsulates a year’s progress in understanding and combating API security threats. It builds upon the foundations laid by the quarterly reports of 2023, offers a comprehensive view of the evolving cybersecurity challenges and the strides made in API security. It is based on analyzing real traffic and tracking common CVEs and bug bounty payouts.
Predictions for 2024 and Beyond
Looking ahead, the report predicts a continued escalation in API security challenges. It anticipates an increase in automated attacks and the potential use of AI by cybercriminals. This section discusses the implications of these emerging trends, advising security professionals on the need to adapt and stay ahead of the curve in their defensive strategies.
In today’s complex digital landscape, the security of APIs has become paramount. As we move into 2024, it’s essential to stay ahead of the evolving API security threats and vulnerabilities. The upcoming webinar on “API ThreatStats™ Report: 2023 Year-In-Review” is your quickest way to learn about the latest trends and insights in API security. The report was created by the Wallarm Research team based on the analysis of: – Over 1.2 billion attacks in the…
I recently hosted and moderated a distinguished panel of Chief Information Security Officers (CISOs) – Nitin Raina, CISO at ThoughtWorks, Mike Wilkes, former CISO at Marvel and Yogesh Badwe, CSO at Druva. We discussed major trends for 2024 across an array of topics including the evolving threat landscape, recent regulations, data privacy considerations, securing product and critical infrastructure. We also discussed strategy, leadership, resilience, scapegoating CISOs, artificial intelligence(AI) and much more. Trend #1: CISO Fallout…





